蘋果Mac電腦再曝密碼繞過漏洞
|
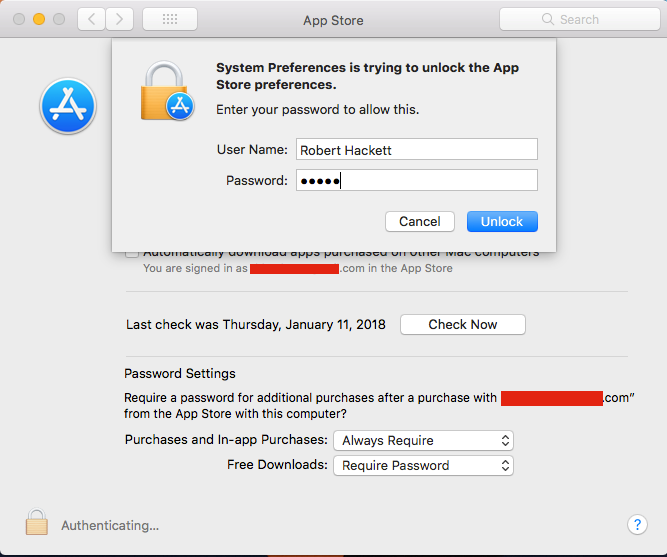
運(yùn)行蘋果最新版High Sierra操作系統(tǒng)的蘋果Mac計(jì)算機(jī)曝出漏洞,可以讓任何人輸入任意密碼來解鎖并修改應(yīng)用商店的偏好設(shè)置。 蘋果在去年11月末也曝出了漏洞:只需輸入用戶名“root”,并進(jìn)入Mac電腦系統(tǒng)偏好菜單“用戶與群組”欄目,便可獲得蘋果Mac電腦更高的管理員權(quán)限。因此,這一漏洞與其相比可謂是小巫見大巫。在打補(bǔ)丁之后,11月底發(fā)現(xiàn)的這個(gè)安全漏洞可以讓任何人對(duì)電腦進(jìn)行物理訪問,并查看任何文件或修改和重設(shè)其他用戶的任何密碼。 新漏洞由IT系統(tǒng)管理員艾瑞克·霍爾塔曼發(fā)現(xiàn)并上傳至漏洞報(bào)告網(wǎng)站Open Radar。不管怎么樣,這個(gè)漏洞也引起了人們的不安。雖然它的嚴(yán)重性遠(yuǎn)不及上一個(gè)漏洞,但也讓人們開始對(duì)蘋果的安全設(shè)計(jì)產(chǎn)生了質(zhì)疑,畢竟這是近幾個(gè)月來發(fā)現(xiàn)的第二個(gè)登錄小漏洞。 致力于報(bào)道蘋果的博客MacRumors首先公布了霍爾塔曼在上周二發(fā)布的貼文。 利用這一漏洞的步驟如下: 1. 打開“系統(tǒng)偏好”。 2. 選擇“應(yīng)用商店” 。 3. 點(diǎn)擊掛鎖標(biāo)志來“解鎖”(如果處于“未解鎖”狀態(tài))。 4.? 點(diǎn)擊掛鎖標(biāo)志解鎖。 5.輸入你的用戶名和任意密碼。 屏幕上將顯示以下提示信息: |
Apple Mac computers running the latest version of Apple’s High Sierra operating system have a flaw that lets just about anyone unlock and edit a person’s App Store preferences with any password. The vulnerability isn’t nearly as bad as one discovered in late November that allowed anyone to obtain higher, administrative privileges on Apple Mac computers merely by entering the username “root” while logging into the “User & Groups” section of a Mac computer’s System Preferences menu. That earlier security hole, since patched, enabled anyone with physical access to a machine to view any files or change and reset any passwords for other users. The new flaw, uncovered by Eric Holtam, an IT systems administrator, and posted to Open Radar, a bug-reporting website, is troubling nonetheless. The finding, though far, far less serious than the past blunder, raises concerns about Apple’s (AAPL, +0.57%)security design, given that this is the second trivial login bug to come to light in recent months. MacRumors, a blog devoted to Apple coverage, first spotted Holtam’s post on last?Tuesday. Here are the steps to follow to exploit the hole: 1.Open “System Preferences”. 2.Select “App Store” . 3.Click the padlock icon to “l(fā)ock” it (if it is “unlocked”). 4.Click the padlock icon to “unlock” it. 5.Enter your user name and any password. Here’s what the screen should display: |
|
在解鎖應(yīng)用商店偏好之后,人們可以更改某些密碼設(shè)置,例如在批準(zhǔn)應(yīng)用相關(guān)購(gòu)買時(shí)系統(tǒng)要求用戶輸入密碼的頻率。即便如此,攻擊者也無法隨心所欲地去進(jìn)行修改,因?yàn)橹挥小笆冀K要求輸入”或“15分鐘后要求輸入”這兩個(gè)選項(xiàng)。 嚴(yán)重警告:任何希望利用這一驗(yàn)證繞過漏洞的人必須以管理員的身份登錄電腦。當(dāng)《財(cái)富》雜志在2015年Macbook Air筆記本上使用非管理員賬戶測(cè)試這一漏洞時(shí),所有的嘗試均以失敗告終。 蘋果似乎在即將到來的mac OS High Sierra升級(jí)(10.3.3)的早期版本測(cè)試這一漏洞的補(bǔ)丁。這一問題很有可能在未來的軟件升級(jí)中得到解決。 蘋果并沒有對(duì)評(píng)論要求做出立即回應(yīng)。(財(cái)富中文網(wǎng)) 譯者:馮豐 審稿:夏林 ? |
After unlocking App Store preferences, a person can tweak certain password settings, such as the frequency with which a system asks for a user’s password when approving app-related purchases. Even so, attackers cannot go on prolonged spending sprees: the two options are “Always require” or “Require after 15 minutes.” One big caveat: anyone looking to take advantage of this authentication sidestep has to be logged in as an administrator. When Fortune tested the approach on a 2015 Macbook Air using a non-administrator account, all attempts failed. Apple appears to be testing a patch for the bug in an early version of a coming macOS High Sierra upgrade (10.3.3). It’s likely the issue will be resolved in a future software update. Apple did not immediately reply to a request for comment. |
-
熱讀文章
-
熱門視頻











